Global Mobility
COVID-19: The Cybersecurity Threat that Shook the World

Since the global pandemic, a horde of new and evolving threats have caused the cybersecurity industry to be on high alert. Sophisticated cyberattacks involving malware, phishing, machine learning and artificial intelligence, cryptocurrency, and more have placed the data and assets of corporations, governments, and individuals at constant risk.
COVID-19 can be classed as the largest ever cybersecurity threat. Perfectly summed up by Mohamed al-Kuwaiti, Head of UAE Government Cyber Security, at a CNBC-moderated panel at the Gulf Information Security Expo and Conference in Dubai December 2020, he said COVID-19 “is a cyber pandemic, not only a biological pandemic.” Here, we deep-dive into this growing threat and provide tips for how to stay safe and vigilant against cyberattacks.
The cyber pandemic
Over the past year there have been reports of scams impersonating public authorities (such as the World Health Organisation and the United Kingdom’s HMRC) as well as attacks on different industries, from oil and gas (US Colonial Pipeline attack in May 2021 and Braskem in Brazil in October 2020) to media (Channel 9) to hospitals all over the globe.
Why is there such an increase of attacks occurring? It’s simple. Since more people are now working from home, there is more time spent online for activities such as work, shopping, socialising, and streaming. The number of devices that are now connected to the internet in the last year has also increased, especially as more organisations have had to ensure their staff have appropriate equipment to enable remote work. This has led to cyberattackers working overtime to create believable scams that are easier for people to become victims. Such scams can be sent by text or e-mail, and in most cases a URL pointed to a fake institutional website which requests debit/credit card details.
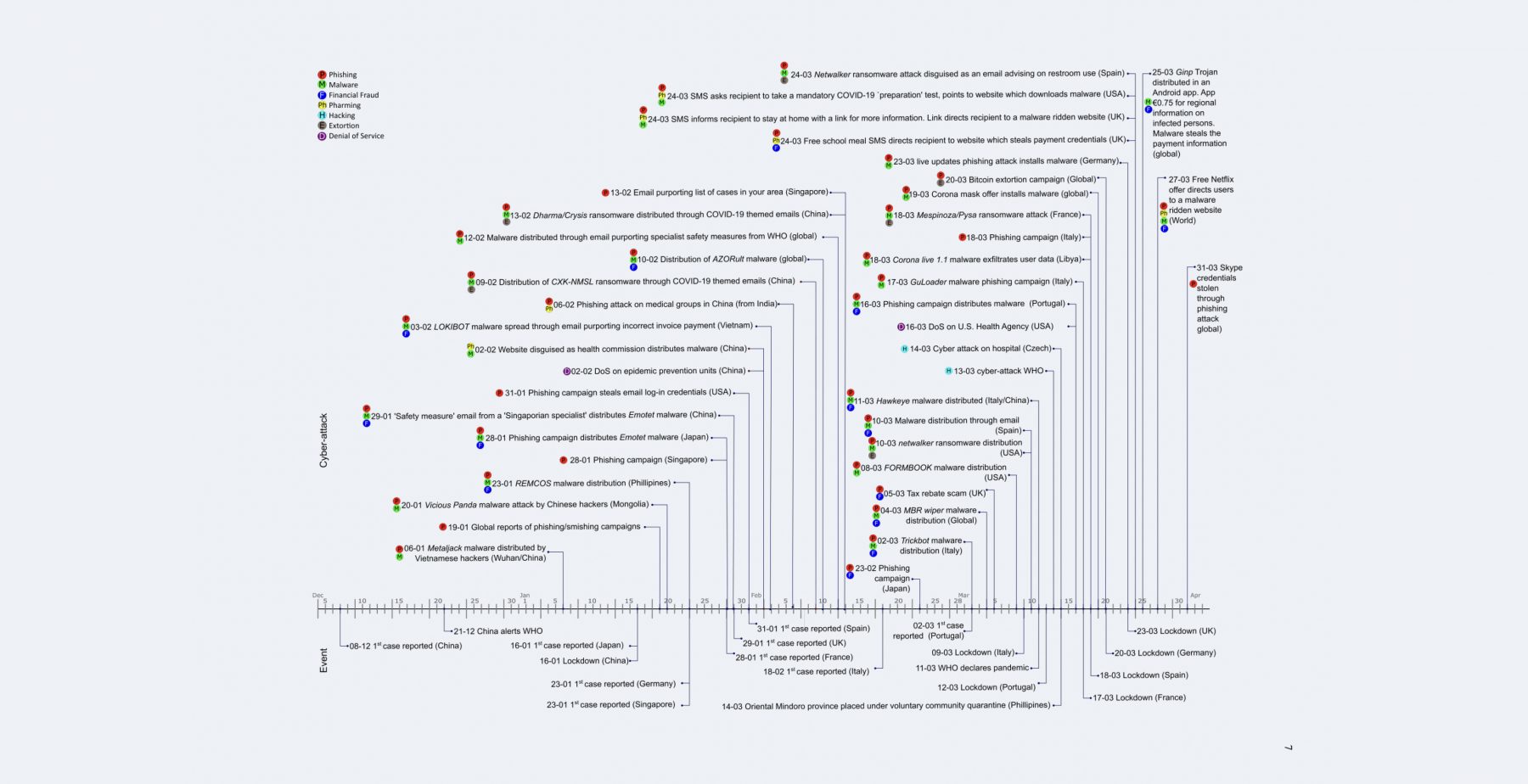
Research from WMG, University of Warwick, Abertay University, University of Kent, University of Oxford, and University of Strathclyde states whenever the virus broke out in a country, a cyberattack followed. From the point that the first case was announced in China (December 2019), the first reported cyberattack was 14 days later. From this point onward the timeframe between virus outbreaks and cyberattacks reduced dramatically. In order to support the research, the universities have proposed a novel timeline of 43 cyberattacks related to the COVID-19 pandemic (fig 1).
The most common COVID-19 related cyberattacks
According to Cybersecurity Ventures, the damage related to cybercrime is projected to hit $6 trillion annually during 2021. They also expect global cybercrime costs to grow by 15% per year over the next five years, reaching $10.5 trillion USD annually by 2025 – up from $3 trillion USD in 2015.
To understand what it is that is causing the financial spike in damages, here are the top examples of the various cybercrimes:
- Malicious domains: There has been an increase in domains registered with the keywords ‘COVID’ or ‘corona’ to take advantage of the growing number of people searching for information about COVID-19. Many of these are developed with malicious intent – by the end of March 2020, more than 2,000 malicious and 40,000 high-risk newly registered domains were discovered, according to Palo Alto Networks.
- Online scams and phishing: Cybercriminals are creating fake websites related to COVID-19 to entice victims into opening malicious attachments or clicking phishing links, resulting in identity impersonation or illegal access to personal accounts. Also, Trend Micro reported that nearly one million spam messages have linked to COVID-19 since January 2020.
- Business Email Compromise: BEC has become the scheme of choice, involving the spoofing of supplier and client email addresses – or use of nearly identical email addresses – to conduct attacks. As organisations heavily rely on the use of third party suppliers, it provides an ideal scenario for criminals to harvest details or to divert millions of dollars of procurement funds into criminal accounts.
- Data-harvesting malware: Data-harvesting malware (such as Remote Access Trojan), info stealers, spyware, and banking Trojans infiltrate systems using COVID-19 related information as a lure to compromise networks, steal data, divert money, and build botnets.
- Disruptive malware: Cybercriminals are deploying disruptive malware like ransomware and distributed denial-of-service (DDoS) against critical infrastructure and response institutions such as hospitals and medical centres, which are overwhelmed with the health crisis. Such malware attacks do not typically aim to steal information but instead prevent the access of critical data or disrupt the system, exacerbating an already dire situation in the physical world. Colonial Pipeline paid the hackers who shut down some of its networks nearly $5 million in ransom in order to get back online.
The vulnerability of working from home
Threat actors are exploiting vulnerabilities in systems, networks, and applications used by businesses, governments, and schools to support staff who are now working remotely. As the growing number of people relying on online tools overburdens the security measures put in place prior to the virus outbreak, offenders search for more chances of exposure to steal data, make a profit, or cause disruption.
To support the alleged figures from Cybersecurity Ventures, the following are statistics that paint a picture of how much of an impact COVID-19 has played technologically:
- 88% of organizations worldwide experienced spear phishing attempts in 2019. (Proofpoint)
- 68% of business leaders feel their cybersecurity risks are increasing. (Accenture)
- On average, only 5% of companies’ folders are properly protected. (Varonis)
- Data breaches exposed 36 billion records in the first half of 2020. (RiskBased)
- 86% of breaches were financially motivated and 10% were motivated by espionage. (Verizon)
- 45% of breaches featured hacking, 17% involved malware, and 22% involved phishing. (Verizon)
- Between January 1, 2005 and May 31, 2020, there have been 11,762 recorded breaches. (ID Theft Resource Center)
- The top malicious email attachment types are .doc and .dot which make up 37%, the next highest is .exe at 19.5%. (Symantec)
- An estimated 300 billion passwords are used by humans and machines worldwide. (Cybersecurity Media)
- Local government domain administrator accesses are sold for an average of $3,217 in 2020. (Digital Shadows)
- The search term “how to remove a virus” increased by 42% in March 2020. (Google Trends)
- 47% of employees cited distraction as the reason for falling for a phishing scam while working from home. (Tessian)
- Scams increased by 400% over the month of March 2020, making COVID-19 the largest-ever security threat. (ReedSmith)
- Half a million Zoom user accounts were compromised and sold on a dark web forum. (CPO Magazine)
How COVID-19 became cyber threat
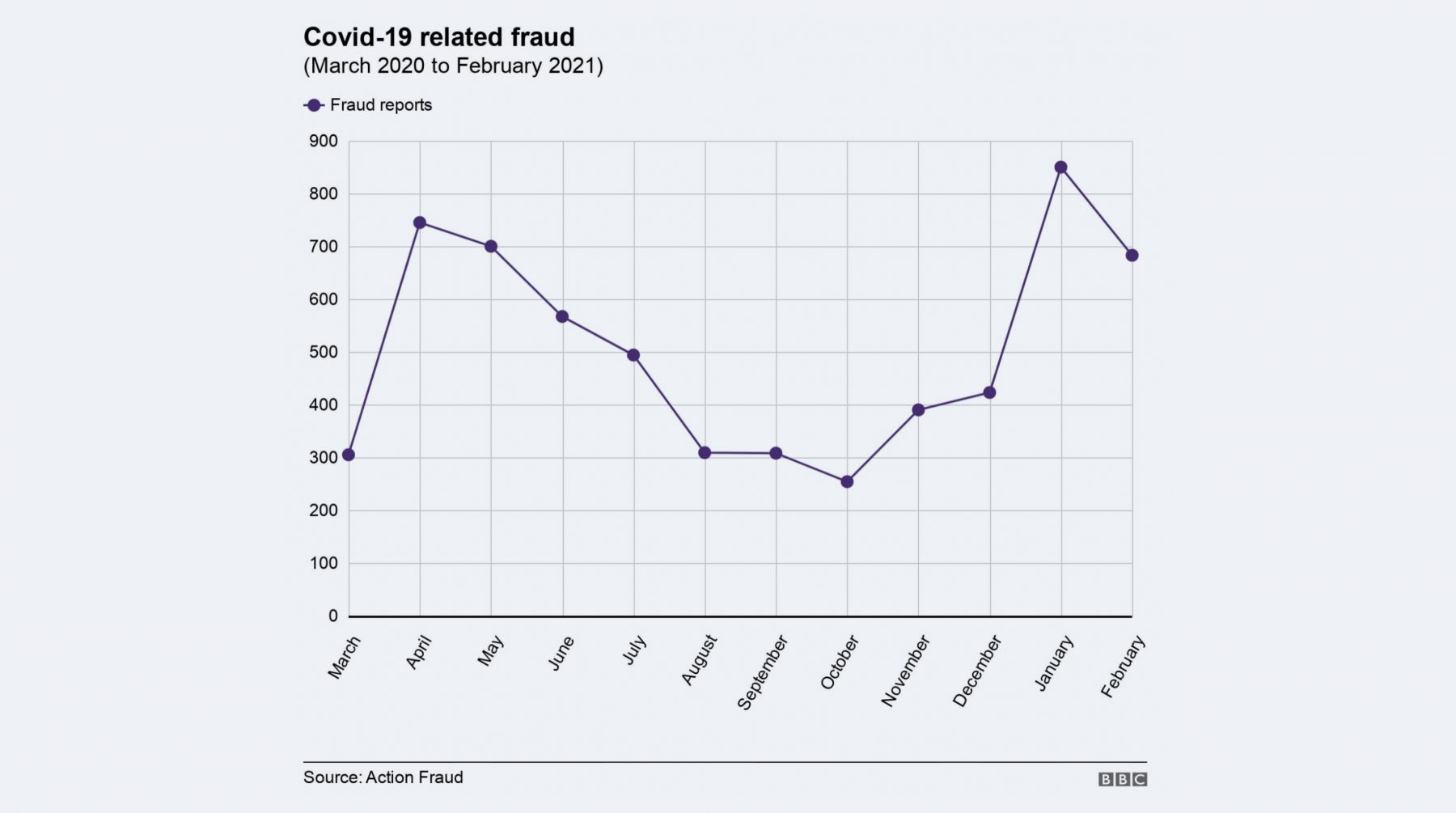
From May 30, 2020 to May 10, 2021, an image (Fig 2.) from McAfee’s Live COVID-19 Malicious File Detection Map states the following top 15 countries are the ones with the most malicious detections according to their software.
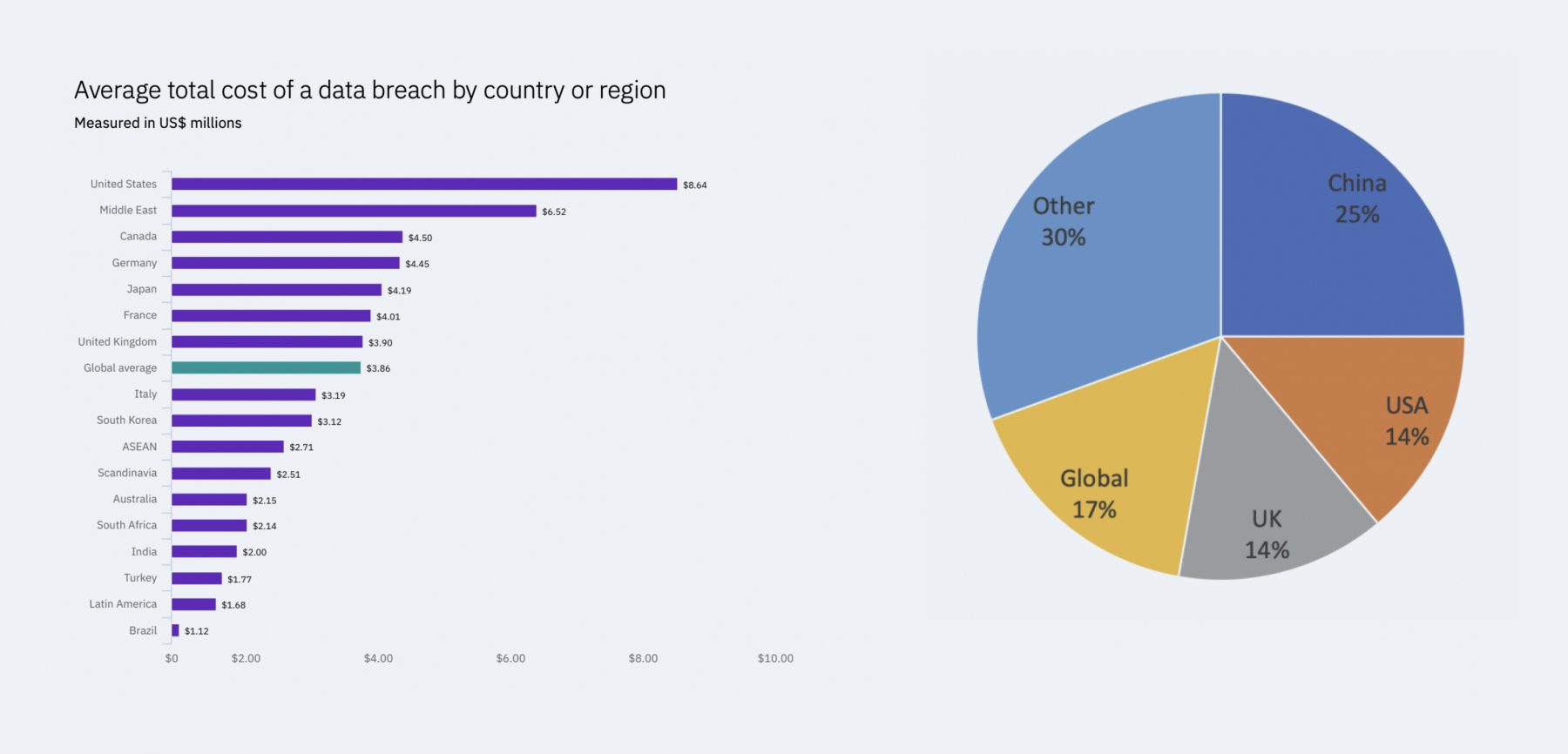
According to SC Media, 65% of organisations in the US admitted to achieving zero-to-minimal compliance of United States data privacy and security regulations. This shocking claim supports a report published by IBM which states In IBM’s 2020 Cost of a Data Breach Report (Fig 3); Organizations in the United States had the highest average total cost at $8.64 million, followed by the Middle East at $6.52 million. In contrast, the average cyber breach costs companies $3.86 million and takes 280 days to identify and contain. Latin American and Brazilian organizations had the lowest average total cost at $1.68 million and $1.12 million, respectively.
COVID-19 themed attacks in the United States largely followed the global attack trend. The initial ascent began mid-February 2020 after the World Health Organization (WHO) officially named the virus. The WHO also warned of fraudulent emails sent by criminals posing as the WHO. This followed a warning from the US Federal Trade Commission about scammers spreading phishing “clickbait” via email and social media, as well as creating fraudulent websites to sell fake antiviral equipment.
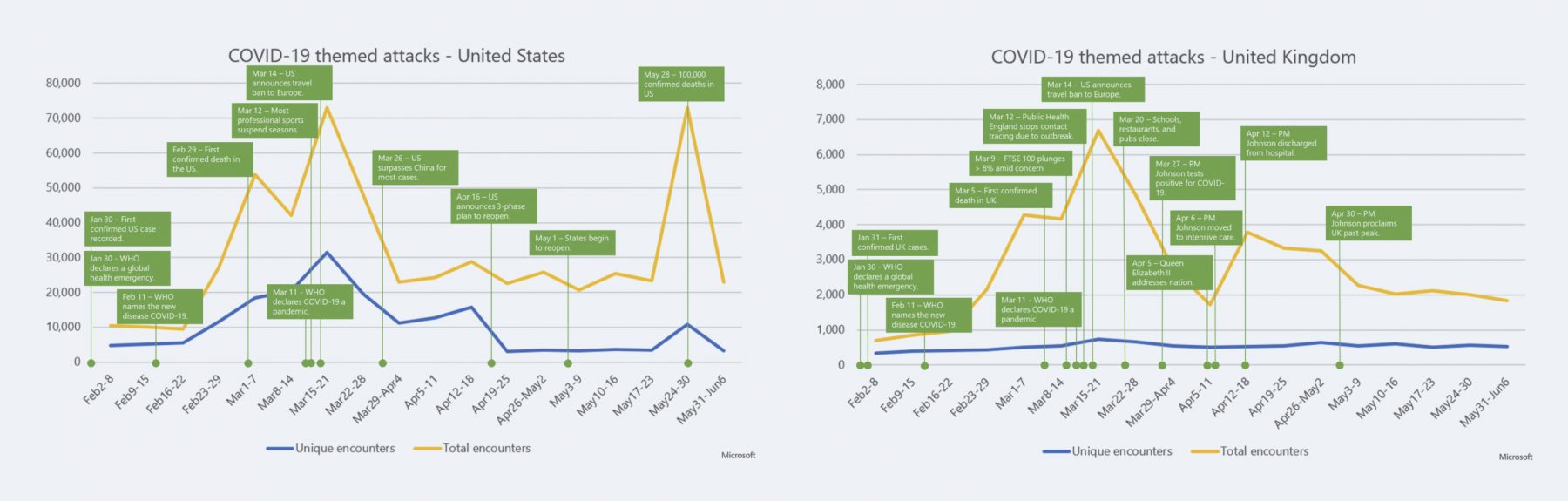
Attacks reached their first peak at the end of February 2020, coinciding with the first confirmed COVID-19 death in the US, and hit its highest point by mid-March 2020, coinciding with the announced international travel ban. The last half of March saw a significant decrease in themed attacks. Telemetry from April 2020 and May 2020 shows themed attacks levelling off between 20,000 and 30,000 daily attacks. The same pattern of themed attacks mirroring the development of the outbreak and local concern likely played out at the state level, too.
Payments to ransomware attackers rose 337% from 2019 to 2020, reaching more than $400 million worth of cryptocurrency, according to figures just released by Chainalysis, a blockchain analysis company.
So far in 2021, hackers have raked in more than $81 million. The average ransom payment has risen from $12,000 in the fourth quarter of 2019 to $54,000 in the first quarter of this year.
Chainalysis notes these figures are conservative because they are based on reported attacks and payments, meaning the actual sum could be astronomically higher due.
In the latter half of March, the United Kingdom increased transparency and information to the public as outbreak protocols were implemented, including the closure of schools. The attacks dropped considerably all the way to April 5, until April 12, the day Prime Minister Boris Johnson was discharged from the hospital due to catching COVID. The level of themed attacks then plateaued at about 3,500 daily attacks until roughly the end of April 2020. The UK government proclaimed the country had passed the peak of infections and began to restore a new normalcy. Attacks took a notable drop to around 2,000 daily attacks.
Worldwide impacts
The impacts of COVID-19 cyberattacks are worldwide. Here are some examples of how other countries outside of the US and UK have been impacted by a cyber-related attack.
- Poland & Germany: In April 2021, a hacking group compromised the social media accounts of Polish officials and used them to disseminate narratives critical of NATO. German authorities have reported that the same group has also attempted to compromise members of the Bundestag and state parliament.
- France: Security researchers found that the number of attacks hitting critical French businesses increased fourfold in 2020 during the COVID-19 pandemic.
- New Zealand: In January 2021, unidentified hackers breached one of the data centers of New Zealand’s central bank.
- Czech Republic: A cyberattack on Brno University Hospital shut down its entire IT network. (Europol)
- India: The country’s National Cyber Security Coordinator announced that cybercrimes in India cost almost $17 billion in 2019.
- APAC: From January to July 2020, there were a total of 216,001 network attacks in the Asia-Pacific region. (WatchGuard)
- Japan, Indonesia, Italy: In January 2020, attackers spread the Emotet banking trojan by posing as a state welfare provider to distribute infected Word documents. Similar operations have been observed in Indonesia, the US, and Italy, with attackers attempting to spread the Lokibot infostealer, Remcos RAT, and other malware.
Tips to keep safe
Falling victim to a cybercrime is unfortunately becoming more common, and as mentioned above it is also becoming costly to victims worldwide. At AltoVita we want to help ensure all of our clients, customers, suppliers, and our staff do all they can to remain safe and vigilant.
If you are at times unsure about what you should be doing to keep safe, here are some tips to help keep you on the right path.
Keep your information safe
- Backup all your important files, and store them independently from your system (e.g. in the cloud or on an external drive).
- Always verify you are on a company’s legitimate website before entering login details or sensitive information (try to prevent entering login details if you have clicked a link in an email – go direct yourself from a search engine or if you have the website saved in your Favourites).
Check your software and systems
- Ensure you have the latest anti-virus software installed on your computer and mobile devices.
- Strengthen your home network
- Create a separate WiFi network for your guests using a different password to your standard home network; this can be done on most home network WiFi settings.
- Change your guest password on a regular basis to prevent unwanted devices automatically connecting to your network.
- Do not give your admin password to your WiFi settings to anyone (generally on the stick of your WiFi hub).
- Always change admin passwords, especially on third party applications and systems.
- Disable outdated browser add-ons that are no longer used as they could be used as entry points.
- Download mobile apps or any other software from trusted platforms only.
- Perform regular anti virus health scans on your computers or mobile devices.
Be vigilant
- Talk to your family − including children − about how to stay safe online.
- Regularly check and update the privacy settings on your social media accounts.
- Update your passwords and ensure they are strong (a mix of uppercase, lowercase, numbers, and special characters).
- Do not click on links or open attachments in emails which you were not expecting to receive or come from an unknown sender.
- Do not hesitate to double-check and think twice before handing over your credit/debit card details or your username and password.
- If you are using a password manager, be cautious if you have to manually enter your login details if they do not auto populate. This may be a sign the website is fake.
- Be cautious accessing free/ public Wi-Fi without using a tool such as a VPN.
If you believe you are the victim of a crime, alert your local police. Most police and local government bodies have a cyber task force that can assist should you become a victim.
Have any questions about safety and security? Send them to privacy@altovita.com!